Back in November of 2013, Microsoft released a Security Advisory stating that by January of 2016 Microsoft would no longer allow root authorities to issue certificates using the SHA-1 hashing algorithm. As that date has come and gone, most users probably never even noticed anything happening. This is because browsers were quick to adopt the new changes. E-commerce is part of everyday life and no one wants to buy something from a site that their browser says is insecure. However, SSL certificates are used for many other things, including verifying publishers of software and drivers. This is also known as code signing.
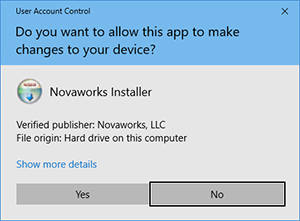 It’s now 2017 and many software publishers still use SHA-1 certificates for their code signing. For websites the change was simple: update the certificate or users would get security errors. For software, it is a little more complicated. Older operating systems like Windows XP, Windows Vista, and Windows Server 2008 do not support SHA256 code signing certificates. This meant changing the certificate may cause problems for users on older systems. To make matters worse, newer operating systems, like Windows 8.1 and Windows 10, do allow SHA-1 certificates but running them may generate extra security prompts for the user. This puts many software publishers on the spot since they are forced to either drop support for older operating systems or have extra security prompts. Applications can be signed with both types of certificates, but this still can cause additional security prompts as one of the certificates is still using SHA-1.
It’s now 2017 and many software publishers still use SHA-1 certificates for their code signing. For websites the change was simple: update the certificate or users would get security errors. For software, it is a little more complicated. Older operating systems like Windows XP, Windows Vista, and Windows Server 2008 do not support SHA256 code signing certificates. This meant changing the certificate may cause problems for users on older systems. To make matters worse, newer operating systems, like Windows 8.1 and Windows 10, do allow SHA-1 certificates but running them may generate extra security prompts for the user. This puts many software publishers on the spot since they are forced to either drop support for older operating systems or have extra security prompts. Applications can be signed with both types of certificates, but this still can cause additional security prompts as one of the certificates is still using SHA-1.
So what do this mean for end-users? Not too much except there may be many software providers who will be quick to drop support for older versions of Windows. This can already be seen as Firefox and Google Chrome have already limited their support of older versions. Here at Novaworks we will not actively support Vista and Windows Server 2008, but we will attempt to maintain compatibility as long as it is feasible. It is important to note that Server 2008 R2 does support SHA256 code signing certificates but does not properly display both certificates if an executable is dual signed.
To verify your version of Windows deals with the different certificates, we have a zip file (download link) that contains the same executable file signed with different certificates. The executable is a simple program that shows if the computer trusts the executable as well as the certificate hashing algorithm. The executable files require the .NET framework 3.5 or later to run.
What does a Code Signing Certificate do?
Much like a certificate for a website, a code signing certificate is issued by a trusted third party. That trusted third party verifies the software publisher to varying degrees based on the level of security requested. Since the trusted third party has verified the publisher the end user knows they can trust the publisher. Code signing certificates also offer another layer of protection for end users. The certificate also can show if the code was edited after it was signed. This means a virus or hacker can’t change software to do something else and still have it appear as a valid publisher.
Additional Resources
Microsoft Security Advisory 2880823 (technet.microsoft.com)
Windows Enforcement of SHA1 Certificates (technet.microsoft.com)
 It’s now 2017 and many software publishers still use SHA-1 certificates for their code signing. For websites the change was simple: update the certificate or users would get security errors. For software, it is a little more complicated. Older operating systems like Windows XP, Windows Vista, and Windows Server 2008 do not support SHA256 code signing certificates. This meant changing the certificate may cause problems for users on older systems. To make matters worse, newer operating systems, like Windows 8.1 and Windows 10, do allow SHA-1 certificates but running them may generate extra security prompts for the user. This puts many software publishers on the spot since they are forced to either drop support for older operating systems or have extra security prompts. Applications can be signed with both types of certificates, but this still can cause additional security prompts as one of the certificates is still using SHA-1.
It’s now 2017 and many software publishers still use SHA-1 certificates for their code signing. For websites the change was simple: update the certificate or users would get security errors. For software, it is a little more complicated. Older operating systems like Windows XP, Windows Vista, and Windows Server 2008 do not support SHA256 code signing certificates. This meant changing the certificate may cause problems for users on older systems. To make matters worse, newer operating systems, like Windows 8.1 and Windows 10, do allow SHA-1 certificates but running them may generate extra security prompts for the user. This puts many software publishers on the spot since they are forced to either drop support for older operating systems or have extra security prompts. Applications can be signed with both types of certificates, but this still can cause additional security prompts as one of the certificates is still using SHA-1.


